Part of understanding Blackhat and Hacker Spam is to put yourself it their mindset. And that means asking “How Can I Use This For My Benefit?”
Well I have been doing a lot of that lately. And one of the genius ideas that I had was full site takeovers. Then I toned it down. And then I thought of smartening it up. And then I thought of scaling it. The result? Well using a simple flaw in WordPress Plugins, and some clever strategy, I could sit back and game 100,000’s of relevant links to my sites, and control them all from one place.

Do This and Face Some Jailtime (source http://www.flickr.com/photos/morganmorgan)
NOTE: This idea is theoretical, and I HAVE NOT actually developed it any further than having a conversation with a few people, including Joost de Valk, regarding the possibility. All my research indicates, and Yoast confirms it, that it is indeed possible to create something this devilish. There are other versions, of this idea floating around, which I will cover as well.
Side Note: This is HIGHLY Illegal. Don’t freaking do it. In fact I am doing blackhat a disservice, this is downright Exploit and Hacking.
While back Yoast warned about a really dodgy SEO plugin being pimped out called Blogpress SEO Plugin. He found that amongst other devious things:
Next to that, the plugin is kind of enough to add a link back to itself on your blog’s homepage, in a hidden div of course, because that’s how smart people roll, right? Luckily, that makes it even easier for Google to find all the sites running the plugin and ban them all in one big sweep.
That is the level of control that you could unleash when you install a third party plug-in to your site.
There are a few things to remember:
- Apart from basic security checks and looking for dodgy programming scripts such as the use of Base 64, not much else is done in the way of security checks.
- WordPress plugins that are not hosted on worpress plugin depository, aren’t put through ANY paces, this includes “Free” and “Paid” plugins.
- There isn’t a verification program for plugins for legitimacy and safety, and anything you install is at your own risk.
- Just because you have used a plugin for years, doesn’t mean that a new update is automatically safe to install.
- Once a plugin is installed, It can do ANYTHING to your site. Remember the Blogpress SEO example above.

Link To Me! (source http://www.flickr.com/photos/hoyvinmayvin/4116728906/)
So I questioned myself on what I wanted to do. Here I am talking to myself:
- What we want: Links
- What type of Links: Thematic, fresh, blog links.
- Are they detectible? Probably, and am guessing easily.
- Boo. So what else do we want? Loads of Thematic 301 redirects.
- Are they detectible? Probably, not too easy to spot all the time, but still.
- Crap, so what else can I use that isn’t detectible? Rel Canonical. Simple command, looks fine to the user, but means a lot to search engines. Users hardly check their code once it’s live as long as page behaves normally.
Note: I have intentionally added a massive flaw to this methodology to trip up people who do ass hat SEO. Learn all search engine directives, what they were meant to do, and what they are capable off. I refuse to elaborate anymore, except that the method I am highlighting is very limited in its effect if you haven’t got a clue what I am talking about in this note.
If I can create a WordPress Plugin that is really popular, and gets installed on thousands of sites, then by simply inserting a backend piece of code, I can control anything on their site.
Easy. Run PPC Ads. Get it ranking in SEO. Pay people to install it, pay bloggers to review it. Make it a really cool plug-in.
Run a search of the WordPress Plugin Directory. Find old plugins no longer updated. Select those that have high installs. Offer to buy from original Author. Boom.
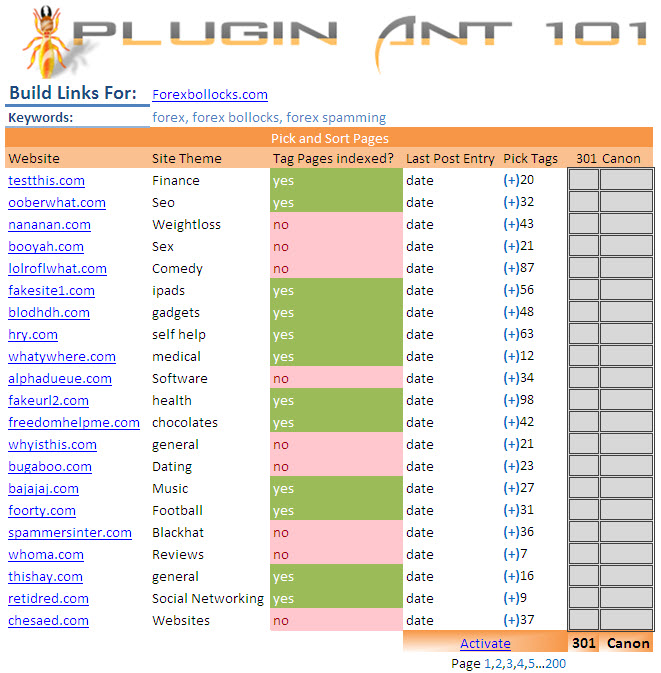
So above is my theoretical tool management centre. What does it do?
- Lists all sites that have the plugin installed
- Lets me pick which site I want to build links for
- Finds all tag pages that aren’t blocked by meta robot or robots.txt per site
- Themes the site by looking at over all keyword density.
- Lets you pick all the tag pages you want by selection
- Highlights when the last post under that tag was
- Let you either pick a rel Canon or a 301 destination for that page.
- One button push

The result could be devastation on all the poor unsuspecting blog owners, or may not even register on their radar! All you are doing is manipulating their tag pages… If you rel Canon them, most blog owners won’t even know anything is wrong except they may lose traffic to their tag pages from the SERPs.
Unlike ordinary category and actual post pages, I have found that these are the least monitored WP pages. Also, for people who love tagging, you can end up with hundreds of variations, hence more pages per site. And apart from those people who have either decent SEO knowledge, or a decent SEO Plugin, tag pages are often left open to search engines.
However this exploit can be used for any part of the site, including actual post page as well as the site home!
Is this a flaw? Yes. Can it happen to you? Yes.
WordPress or at least people passionate about it need to find a way to work on verification of plugins and maybe create a “Trust Worthy” verification for plugin release. Till then, I will rely on my network of people such as Yoast, or freelancer WP Plug-in devs or my Birmingham based Development team who I have worked with for years to test and check anything I install on my sites.
- Injecting Malware.
- Cookie Stuffing.
- Webmaster Tools Takeover.
- Sale hijacks.
- Password and Login Hijacks.

WordPress Condom – Source: http://www.flickr.com/photos/nbachiyski/1463351154/
Don’t install any old crap you find on the internet. Check it. If you suspect a dodgy plugin, contact Yoast who will run a WordPress Plugin Review.
There are many exploits for sites, see this article for instance (by Kristine Schachinger).

Leave a Reply